
In a time where prioritizing the safety of both employees and assets is absolutely essential, Access Control Systems (ACS) have become one of the most important aspects of an organization’s security strategy.
Modern ACS solutions surpass traditional locks and keys, offering a suite of advanced features to deter unauthorized access, monitor activity, and improve physical security measures. However, despite their immense security benefits, implementing and effectively utilizing these systems takes time and effort.
Without a holistic approach to ACS, organizations can miss out on many benefits and become vulnerable to security gaps. In this article, we’ll explain the basics of access control systems and empower you with insights to manage them successfully.
What is an Access Control System?
An Access Control System (ACS) is an electronic system that regulates the entry of individuals or vehicles into a protected area through authentication and authorization processes at designated access points.
Its main goal is to prevent unauthorized access and ensure the safety and security of people and assets within the controlled area. Additionally, ACS offers several benefits beyond security:
- Convenience: Automated access control eliminates the need for manual key management.
- Efficiency: Streamlined access processes save time and resources.
- Scalability: Systems can be easily adapted to accommodate changing needs and user groups.
- Integration: ACS can integrate with other security systems like video surveillance and alarms for a comprehensive security solution.
Now that we have a basic understanding of access control systems, let’s get into some of the details.
Key Components of an ACS
Access control systems may seem complex, but they revolve around four key components that underpin effective security, working together to grant access where and when it’s needed to the right people.
- Door or Entrance: The physical barrier that controls access to a protected area. It’s the entry point where individuals interact with the system to gain access.
- Electrified Door Hardware: A device that receives signals from the Access Control System to lock and unlock doors.
- Card/Biometric Reader: A device that reads credentials (key cards, fobs, mobile devices) presented by individuals seeking access. It communicates with the control panel to verify identity and access permissions.
- Door Contact: A sensor that detects whether the door is open or closed. It sends a signal to the control panel, ensuring security before granting access and monitoring for unauthorized attempts to open the door.
- Request to Exit (REX): A device that allows authorized individuals to exit a controlled area without using a credential. It typically consists of a button or sensor that unlocks the door temporarily for egress.
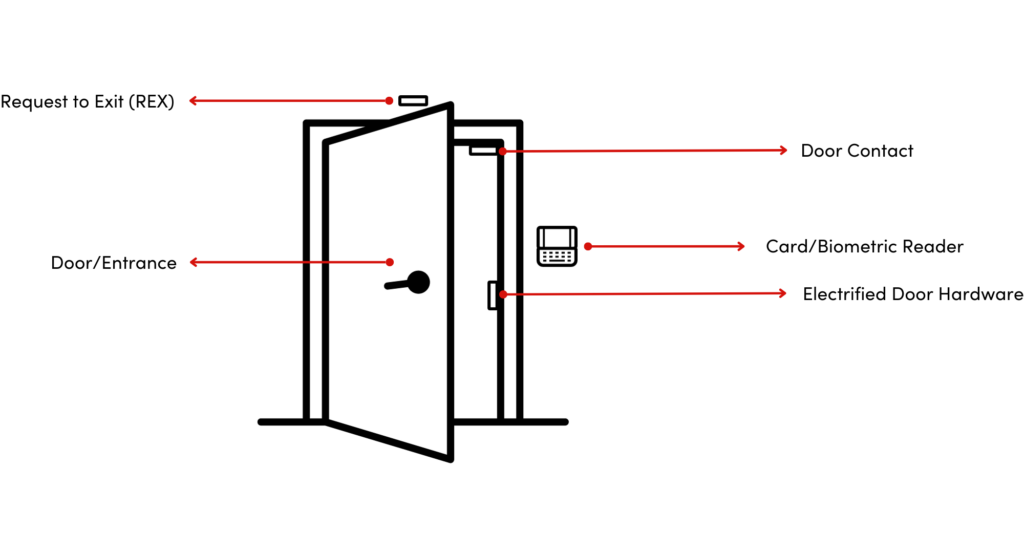
Each component plays a vital role in ensuring the security and efficiency of an access control system, working together to manage access and secure sensitive areas.
Beyond just granting or denying access, these systems can also monitor and record access, restricting entry to certain times or specific individuals. ACS can also integrate with other security systems like video surveillance and intrusion alarms for a more comprehensive safety network.
Types of Access Control Systems
There are various forms of access control systems, and the most effective solution depends on an organization’s specific security requirements. In some cases, a combination of different access control systems may be used to achieve the desired level of security. Some types of access control include:
- Biometric Access Control relies on biological identifiers such as fingerprints, iris scans, facial recognition, or voice patterns, offering high security and removing the need for physical credentials, though it tends to be costlier.
- Keycard/Badge Access Control uses electronic cards or badges with magnetic strips, barcodes, or RFID chips; it’s affordable but can be compromised if credentials are lost or stolen.
- PIN-Based Access Control requiring a personal identification number on a keypad, is simple and inexpensive but vulnerable to attacks like brute force and shoulder surfing.
- Proximity Access Control employs key fobs or RFID cards for hands-free access yet can face cloning and signal jamming risks.
- Mobile Access Control leverages smartphones for access via apps, offering convenience and flexibility but depends on smartphone compatibility and can have security gaps.
Choosing the right access control system for your organization requires careful consideration of several crucial factors. A security integrator can guide you through this process, customizing a solution that fits your unique requirements and integrates smoothly with your current security setup.
Access Control Systems in Leading Industries
Access control systems are widely used across various industries to manage and secure access to restricted areas, data, and resources. Every organization has its own unique needs and challenges that access control systems help to mitigate,
Here are some examples of how different industries utilize access control solutions:
- Healthcare Facilities: In healthcare, access control solutions play a crucial role in ensuring the security of patient information, pharmaceuticals, and medical equipment. Staff are equipped with keycards with varying access permissions, ensuring only the appropriate personnel are granted entry to sensitive areas, and restricting access to individuals such as non-medical staff, students and visitors.
- Financial Institutions: Banks and financial institutions rely heavily on access control to protect valuable assets, sensitive financial data, and customer information. Biometric authentication, card readers, and PIN-based systems are commonly used to grant access only to authorized personnel, minimizing the risk of breaches and fraud.
- K-12 Schools: Educational institutions use access control systems to enhance campus safety and manage access to classrooms and administrative offices. Access cards or keyless entry systems can help prevent unauthorized entry, protect students and staff, and track attendance for security purposes.
- Manufacturing and Industrial Facilities: Access control solutions are vital in manufacturing environments to ensure the safety of employees and maintain the integrity of production processes. These systems can limit access to hazardous areas, machine controls, and critical infrastructure, reducing accidents and theft.
Access Control Best Practices
Administrators managing access control systems, even casually, stand to gain immensely by understanding best practices. This insight is key for identifying system vulnerabilities, enabling proactive security and effectively handling incidents, helping minimize damage and avert future risks.
Here are some actionable best practices to consider:
- Identify and prioritize vulnerabilities: Regularly assess and rank system weaknesses to focus security improvements where they are most needed.
- Set access levels: Define clear access privileges for different users to ensure everyone has appropriate access rights.
- Update user credentials at a system level: Periodically refresh and manage user credentials to maintain system integrity and prevent unauthorized access.
- Work with a top-notch physical security integrator: Partner with experts to stay updated on the latest security technologies and best practices, ensuring your system remains robust and effective.
By implementing these best practices, administrators can significantly enhance the security and efficiency of their access control systems, ensuring a safer and more secure environment for all.
Tailored Access Control Solutions
3Sixty Integrated’s approach to security is unparalleled in the industry, offering a unique blend of cutting-edge solutions and personalized service. Our range of capabilities go beyond basic access control, providing comprehensive, adaptable systems designed for each organization’s specific challenges and needs.
With a focus on future-proofing and innovation, we are dedicated to ensuring that your security measures are effective today and remain robust against tomorrow’s evolving threats.
3Sixty Integrated is a Texas-based systems integrator that specializes in the design, installation, and maintenance of physical security technology. We partner with organizations who want to streamline their electronic security infrastructure. Additionally, as a division of The Cook & Boardman Group, 3Sixty Integrated and our sister branches have a nationwide reach and over 65 years of experience offering total opening solutions, from custom doors, frames and hardware to security integration technology.

